Protect your business from the increasing risk of Cyber Attacks with Attack Surface Management from CSIQ. We help organisations that don’t have an in-house team of qualified security professionals to respond to the latest threats.


What is Attack Surface Management?
Attack Surface Management refers to the exposed areas of your business where an unauthorised person can access a system and collect data. In principle, the smaller the attack surface, the easier it is to protect.
The attack surface is typically considered the following:
- Endpoints & Staff
- Perimeter Firewalls, Internet Connections, and Application Services
- Communication and Telephony Systems
- Identity and Access Management Solutions (Microsoft 365 / Active Directory / G-Suite etc)
- Remote Working Solutions such as Citrix and VPN
- Corporate Website
By monitoring what the internet sees and proactively managing your devices, you gain control and peace of mind to ensure your business is protected from modern cyber threats.
Cyber Security Simplified
Our services are built to be cost-effective while maximising risk reduction. All consultancy and managed solutions provide actionable results that protect your business from opportunistic to advanced persistent threats.
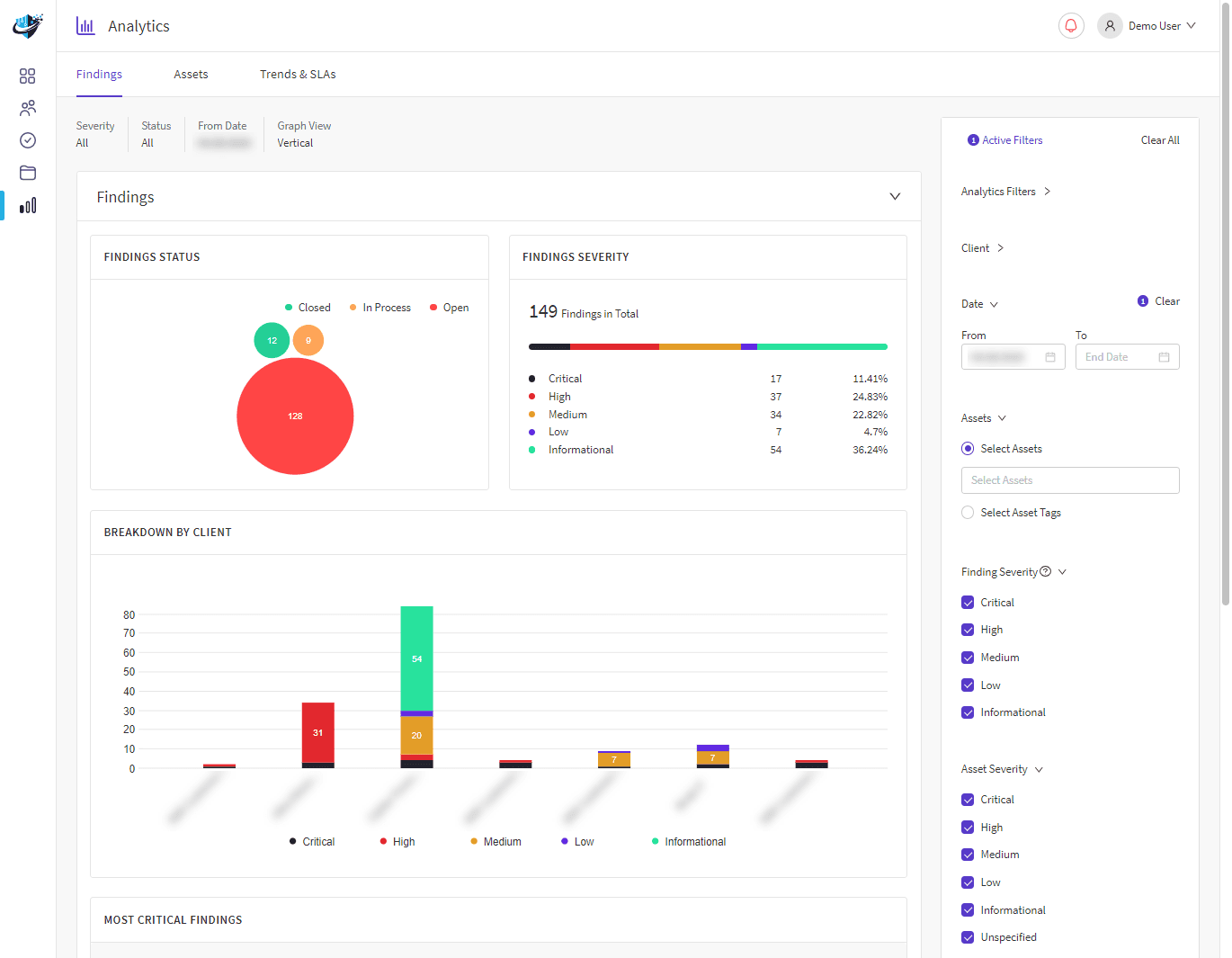
17
32
82
What are the benefits of a Managed Attack Surface?
A hackers perspective of your organisation
Continuous monitoring of your attack surface. Optional Penetration Testing-As-A-Service.
Analytics that guide risk reduction strategies
Access to CSIQ Insight Risk Management Platform and Experts
Managed Attack Surface features:
Public Email Addresses
By understanding which email addresses are public, you can provide focused training for those users to help prevent spam and targeted email attacks.
Email Health
Correct DNS configuration and blacklist monitoring ensure time sensitive delivery of emails to customers and suppliers.
IP Reputation
Monitoring the IP reputation of your company IP addresses provides an indicator of infected machines which are avoiding endpoint protection solutions.
Dark Web Chatter
Commonly used by hackers to share leaked information on individuals and companies, we monitor the dark web for indicators of targeted attacks and information leaks.
Monitored by the SOC Team
All alerts and metrics are vetted and monitored by our SOC team, and all threat metrics alerts are available through our Live Risk Management Platform.
Impersonation Attacks (DMARC/SPF)
We monitor DMARC forensic and aggregate reports to provide insight on email failures and identify if malicious users are attempting to impersonate your users.
DNS Health
DNS is essential for network communication. All businesses utilise this technology to make services such as remote access and the company website accessible to staff and customers, so we monitor for new DNS records and any misconfigurations that could reveal sensitive information.

CSIQ Insight – Live Risk Management Platform
All consultancy and managed services come with access to our Risk Management Portal. All risk types, including technical, human, residual and inherent, are allocated a score, allowing for a strategic approach to risk reduction.
Credential Leaks
We index and aggregate credential leak databases to provide a true reflection of the risks associated with lost credentials.
Search Engine Leaks
Our Threat Hunting team can identify potential information leakage by combining automated and manual assessments of search engine databases.
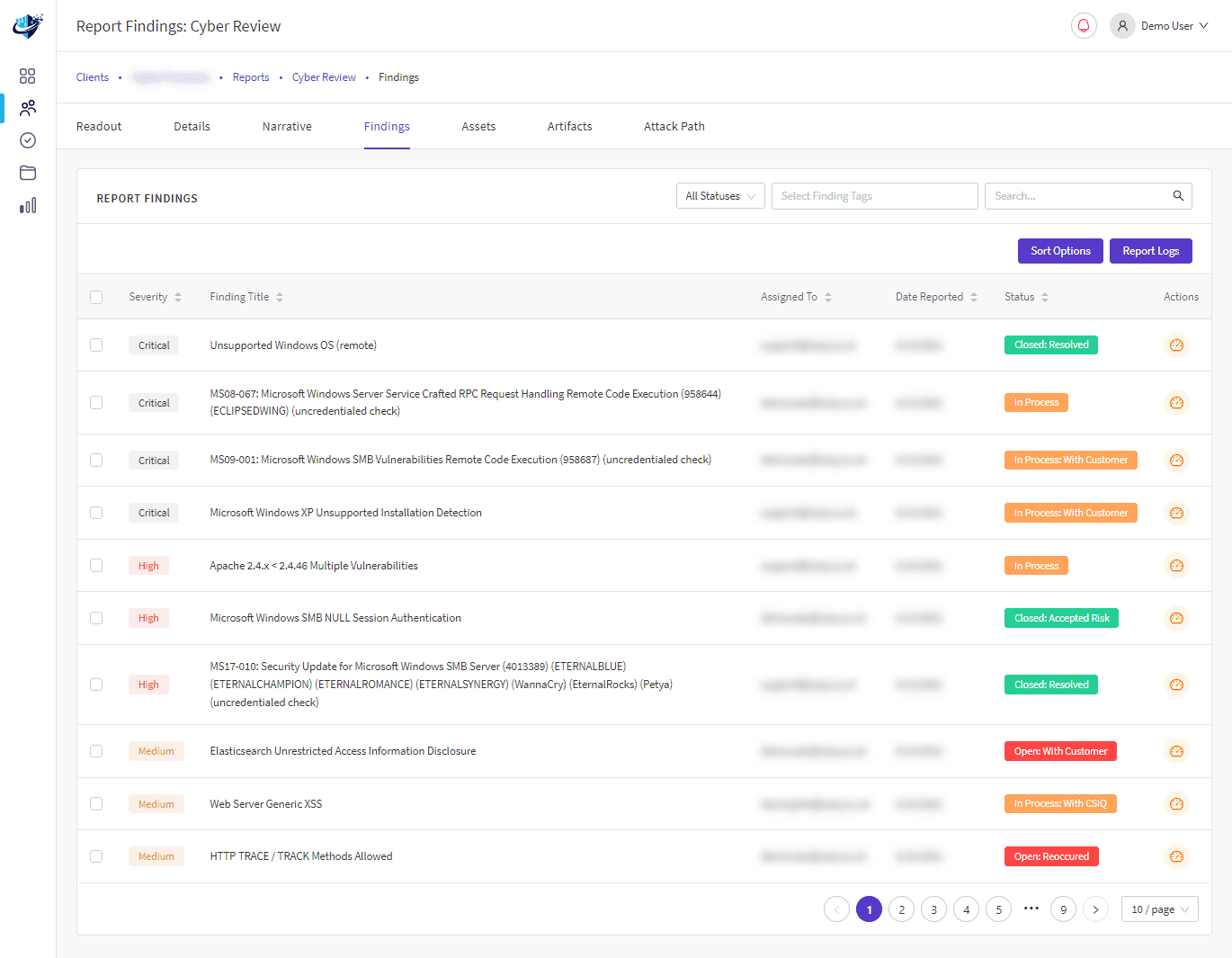
Monthly Reports (Threats and Recommendations)
Monthly reports detailing individual risk scores, a summary of events, detailed vulnerabilities, and security recommendations are provided.
Quarterly Threat Intelligence Report
A manual investigation is performed, and a report is generated to summarise the information collected and provide recommendations where appropriate.
Initial Threat Intelligence Report
During onboarding, we will run a full assessment, manually review the collected information and provide recommendations on reducing the risks identified.

We monitor for indicators of compromise and the following metrics at a minimum:
- Multi-Factor Authentication Is enabled for all accounts
- Disabled Users with a License
- Administrator Added/Removed
- Disabled Administrator Accounts
- Locked out accounts
- Users targeted by brute force attempts
- Standard users logging in with administrator accounts
- Aggregated insights across the platform
Perimeter Vulnerability Scanning
Our recommend methodology will typically consist of weekly scans of all TCP/UDP ports and daily scans against live services consisting of emerging threats and critical vulnerabilities.
Active Directory Security Assessment
Obtaining high-level privileges within Active directory will often result in access to all company information and control over all workstations and servers. Our unique assessment will identify configuration weaknesses and highlight any issues that could result in account compromise.
Onboarding Assessments
Email Health Assessment
We review your current email health and provide recommendations on implementing SPF, DMARC and DKIM correctly and without interruption.
Microsoft 365 and Azure AD Security Assessment
Our consultancy team will perform a security assessment on your Microsoft 365 environment during onboarding. The report will detail health and configuration, identify signs of compromise, and provide recommendations on securing your accounts from the latest threats.
Endpoint Security Assessment
We will conduct an assessment against a typical end-user device and provide recommendations on how to protect against malicious attachments and techniques used by advanced persistent threat actors.


CSIQ Insight: Risk Management Portal
All consultancy and managed services include access to our Risk Management Portal.
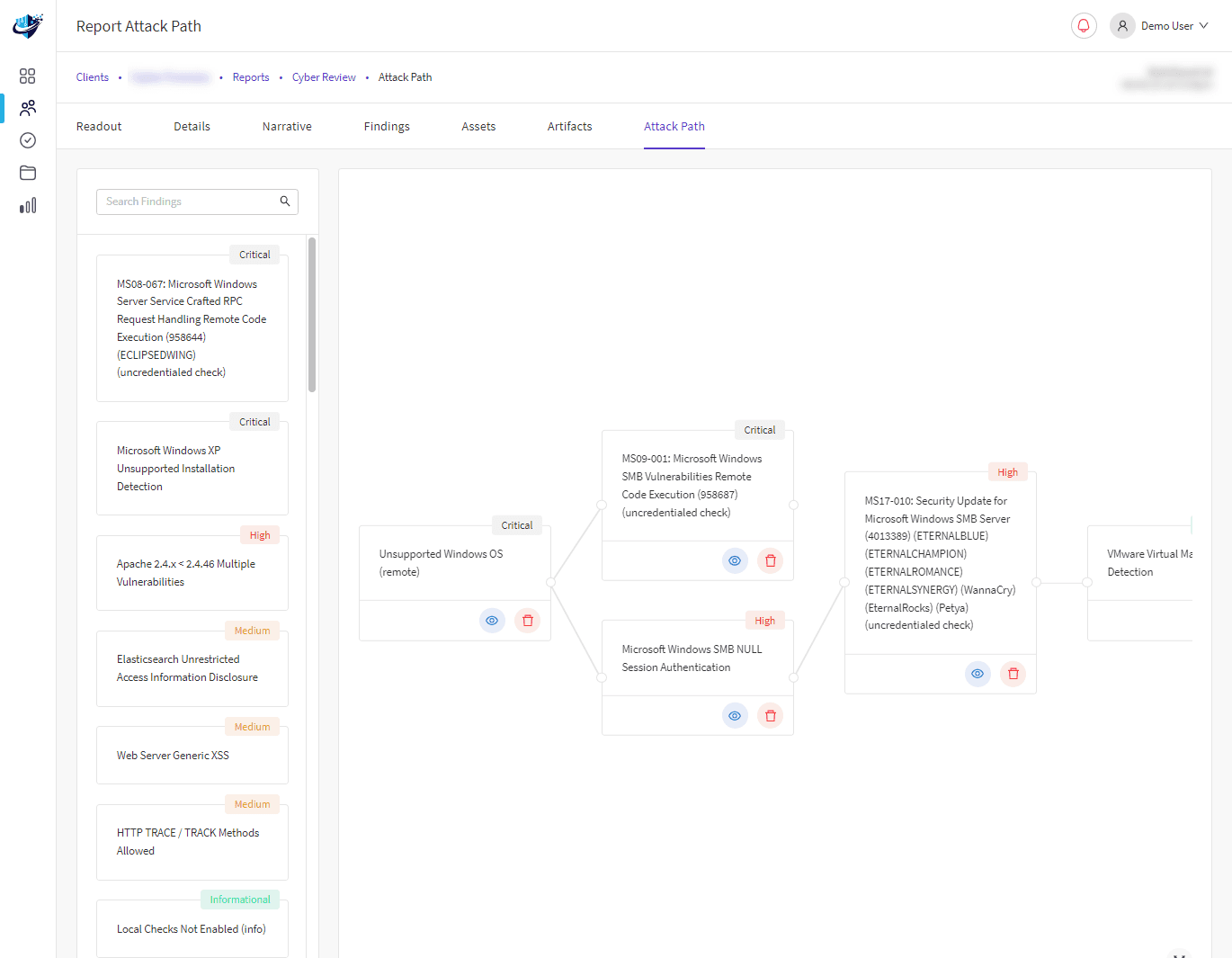
Attack Surface Lifecycle
Security Operations Centre
Our SOC team operate using our Attack Surface Lifecycle to proactively monitor and respond to threats. Ensuring a timely and prioritised approach to risk reduction

Attack Surface Lifecycle
Security Operations Centre
Our SOC team operate using our Attack Surface Lifecycle to proactively monitor and respond to threats. Ensuring a timely and prioritised approach to risk reduction
Plans & Pricing
Stay ahead of cybercriminals with round the clock vulnerability management and complete visibility of your internet facing assets.
Penetration Testing as a Service (PTaaS)
Our Pre-Pay contract combined with Managed Attack Surface enables a proactive approach to protect your organisation from cyberattacks.
Businesses are often stuck in the loop of annual penetration testing and then waiting a year before retesting. With PTaaS, our ongoing services significantly reduce the time it takes to identify, validate, and remediate vulnerabilities.
What are the Benefits of PTaaS?
- Continuous security monitoring to protect against emerging vulnerabilities
- Any new services introduced by the business are automatically assessed
- Managed by our SOC and Consultancy team
- Risk Management Platform – Full view of all identified security issues
- Reduces the time between identified vulnerability to remediation with dedicated support

Flexible Pre-Pay Contract
Benefit from a discounted consultancy rate and rapid response with our Flexible Pre-Pay Contract options
Journey to Adversarial Awareness and Defence
Our methodical and project managed approach ensures you will begin your risk reduction journey and benefit from our proactive monitoring sooner.
Journey to Adversarial Awareness and Defence
Our methodical and project managed approach ensures you will begin your risk reduction journey and benefit from our proactive monitoring sooner.

Cyber
Intelligence Services
Check out our Attack Surface Review page for a point-in-time hackers’ perspective of your organisation.
To learn more about the other Cyber Intelligence service we offer, visit our Cyber Intelligence page.
Or get in touch to discover all our available services.
Our Accreditations & Memberships
We are proud of our industry recognised certifications in Cyber Security and Service Delivery
FAQ
What's included in the endpoint security assessment?
The endpoint security assessment evolves as the tactics and techniques of attackers change.
The following is tested at a minimum:
- MITRE ATT&CK Tests
- Use of Encryption
- Two-Click Rule of downloaded files
- Two-Click Rule of email attachments
- Vulnerability assessment
- Software Restriction Policy / AppLocker Effectiveness
- PowerShell and Remote Management Configuration
- Weaponised document execution
- Macro blocking
- Credential leakage by opening malicious emails and files
- CIS policy compliance
- Data Exfiltration channels
- EDR/AV effectiveness
- Ransomware prevention effectiveness
Do you offer a penetration testing as a service contract?
We do. Our pre-paid contract has many benefits, including a core cyber review and rapid incident response. Still, if you only require PTaaS services, these can be purchased in 10-hour bundles at the same reduced consultancy and engineering rate.
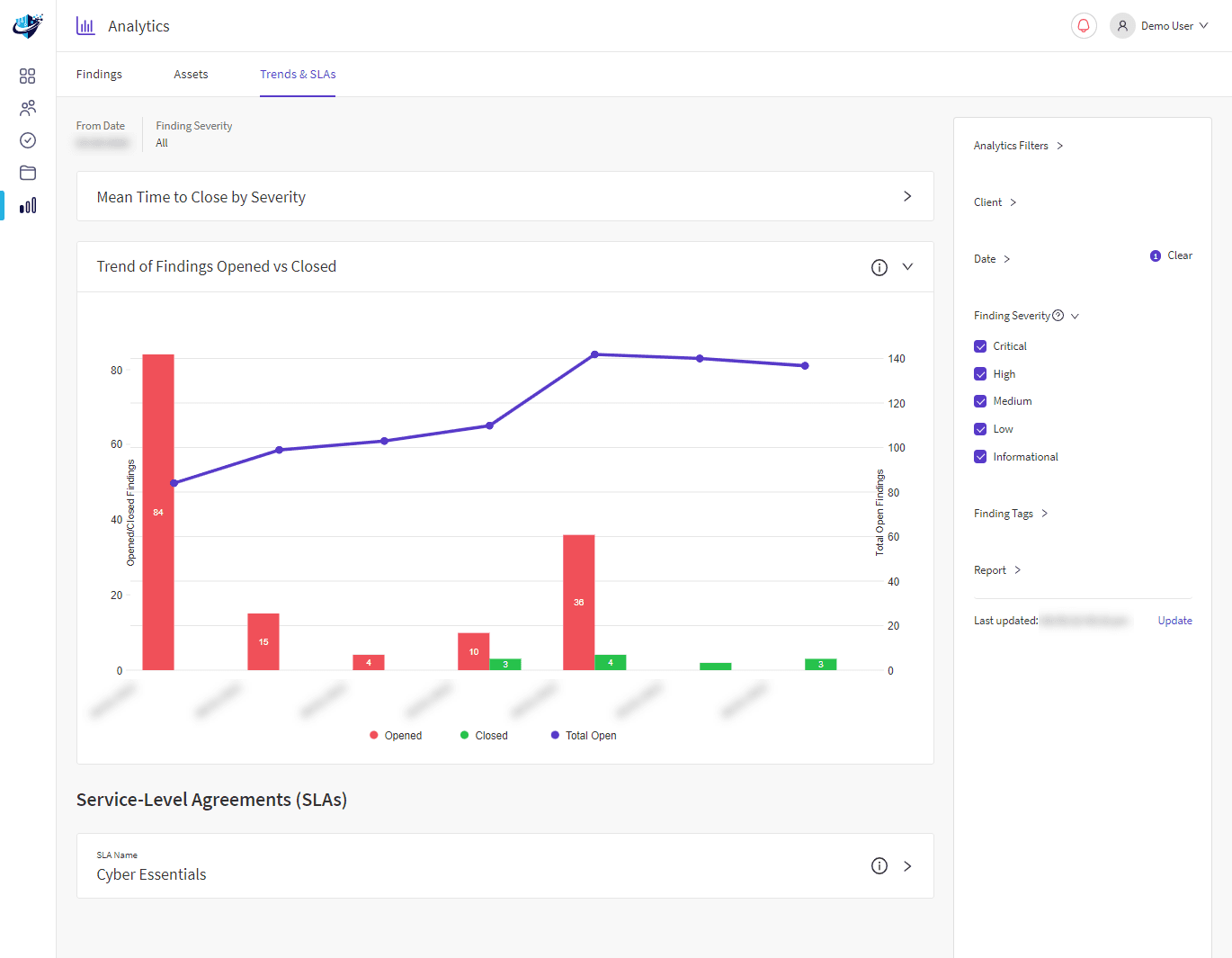
How often are vulnerability scans run?
Our recommended strategy is to run a weekly scan of all TCP/UDP ports for all vulnerabilities and daily scans against all open ports for emerging threats and high/critical vulnerabilities.
This approach ensures a minimal impact on system performance and stability while still maintaining visibility of essential vulnerabilities.
Will Managed Attack Surface help us meet Cyber Essentials Plus?
Our Attack Surface Vigilance package far exceeded Cyber Essentials Plus’s requirements and was designed to help companies protect and respond to modern cyber threats.
CSIQ uses Cyber Essentials Plus approved scanning vendors for all vulnerability assessments. Attack Surface Essentials will help you meet your requirements for external scanning with visibility of all CVSSv3 7.0 and above vulnerabilities.
Have a question for us about our services?
Send us an enquiry to get a rapid response from a cybersecurity expert.
Email Us
Call Us
"*" indicates required fields