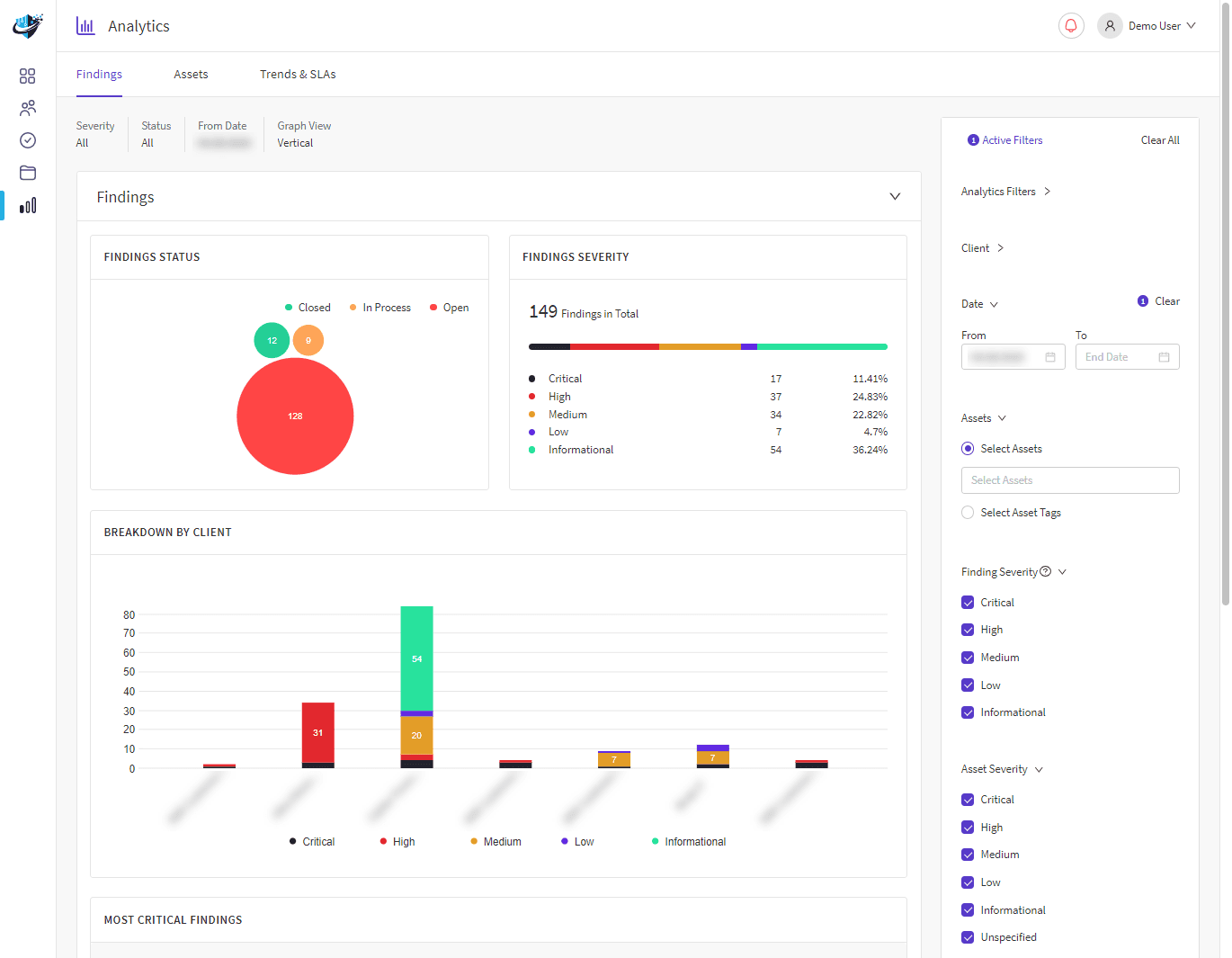
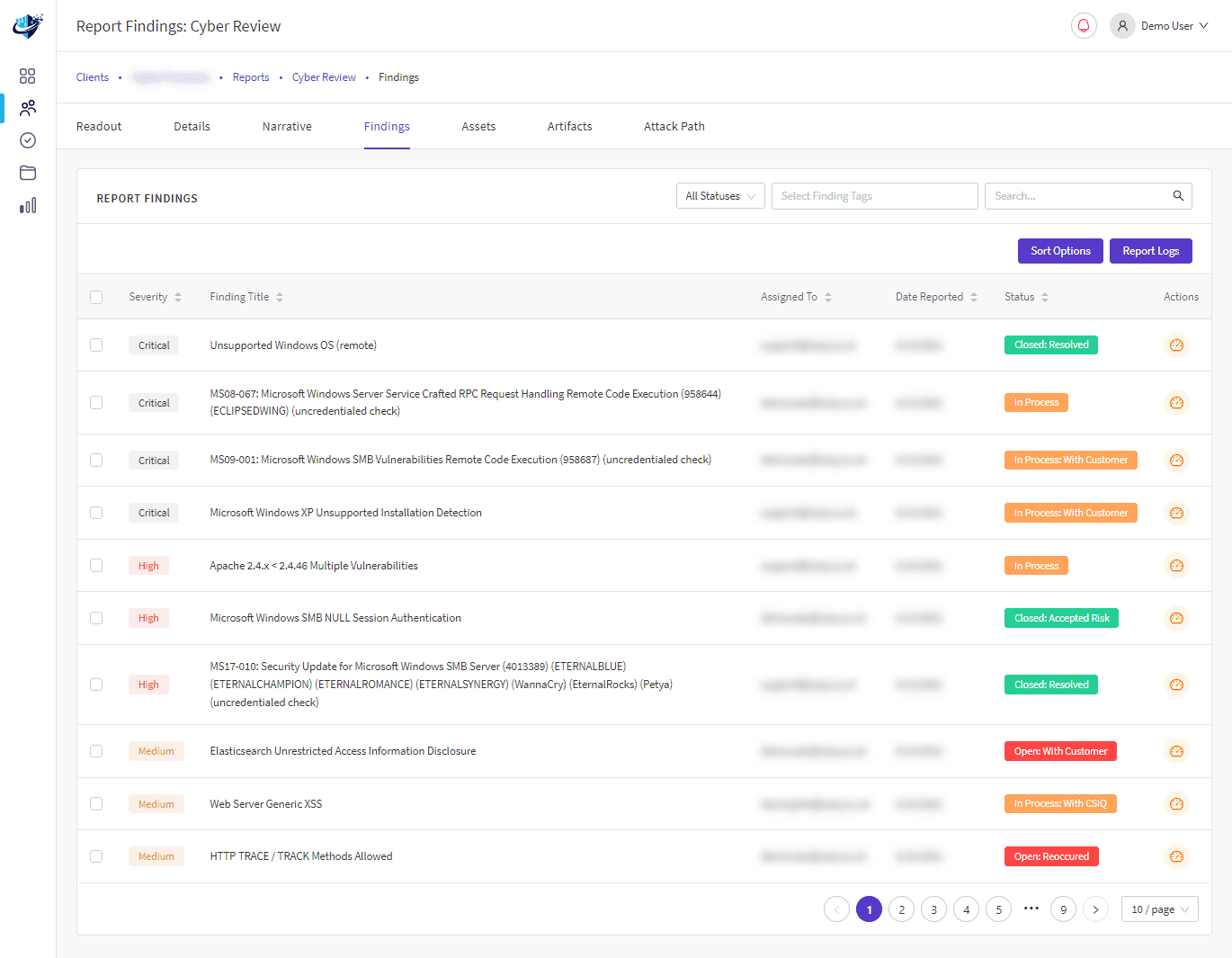
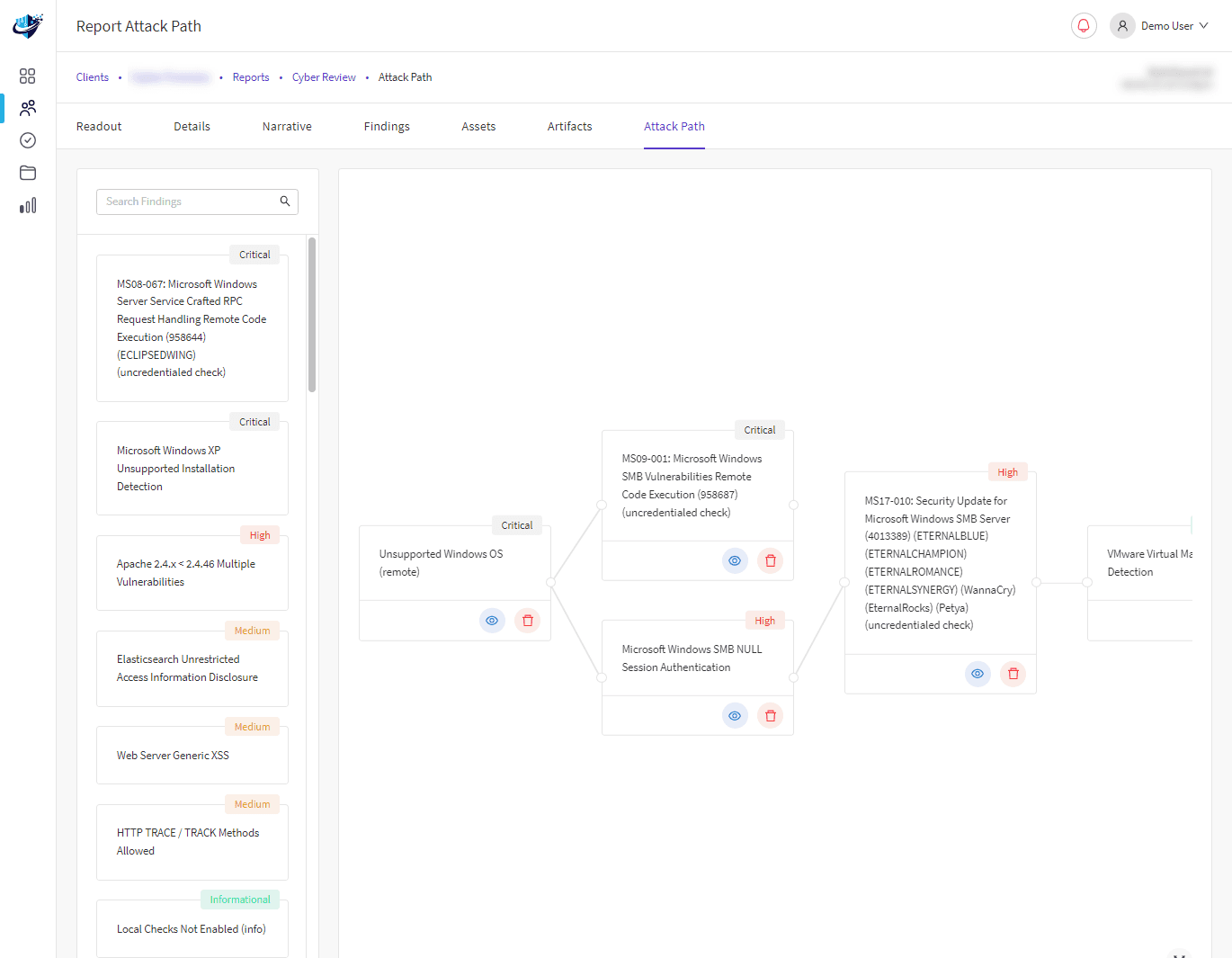
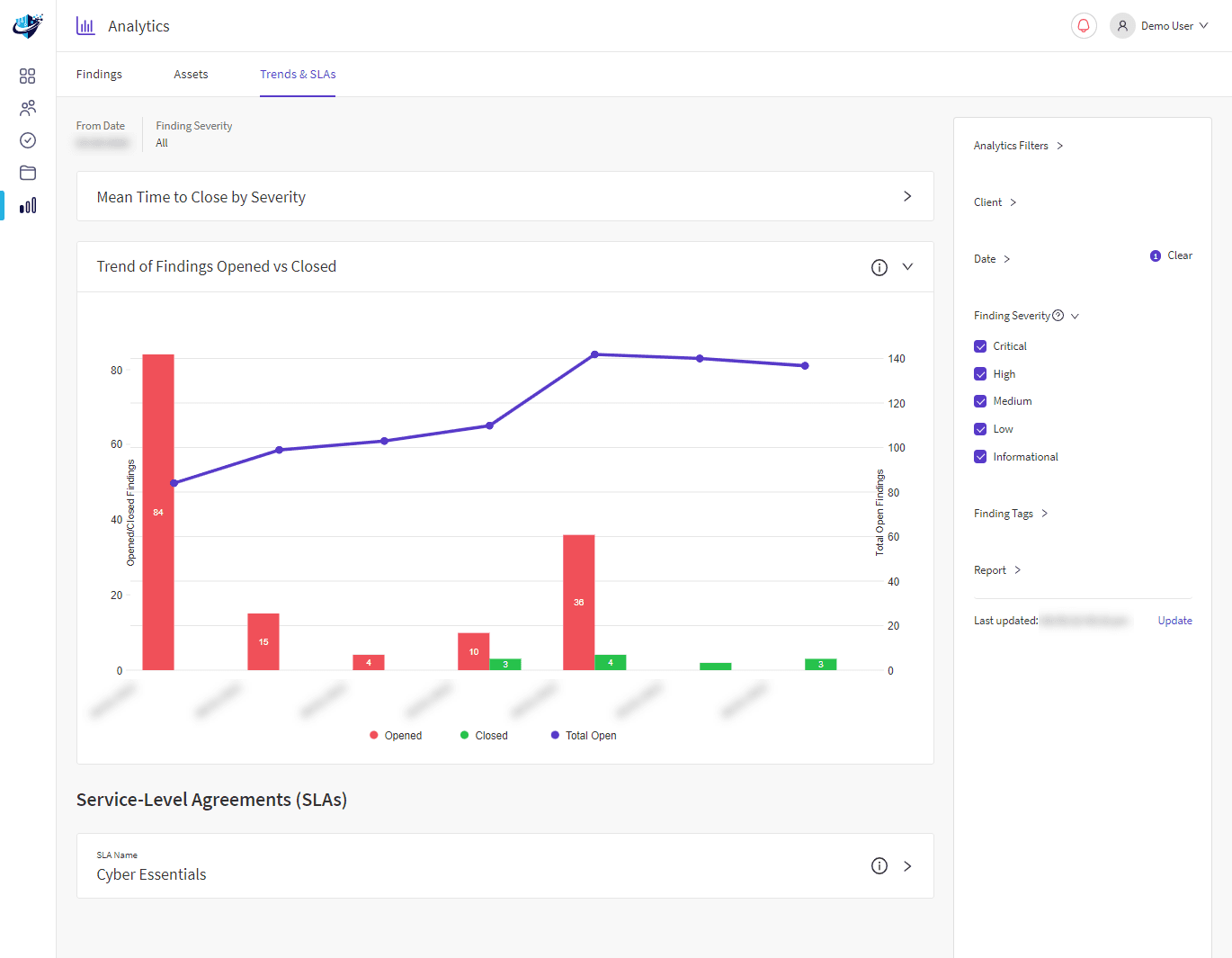
As cyber-attack simulation providers, we incorporate people and technology to create attack scenarios that Advanced Persistent Threats (APT) actors use to access corporate networks.
Following the attack, we will provide an audit timeline to help highlight the issues and weaknesses in your defences. Our approach will ensure your organisation is prepared with the knowledge needed to respond to the evolving threat landscape.