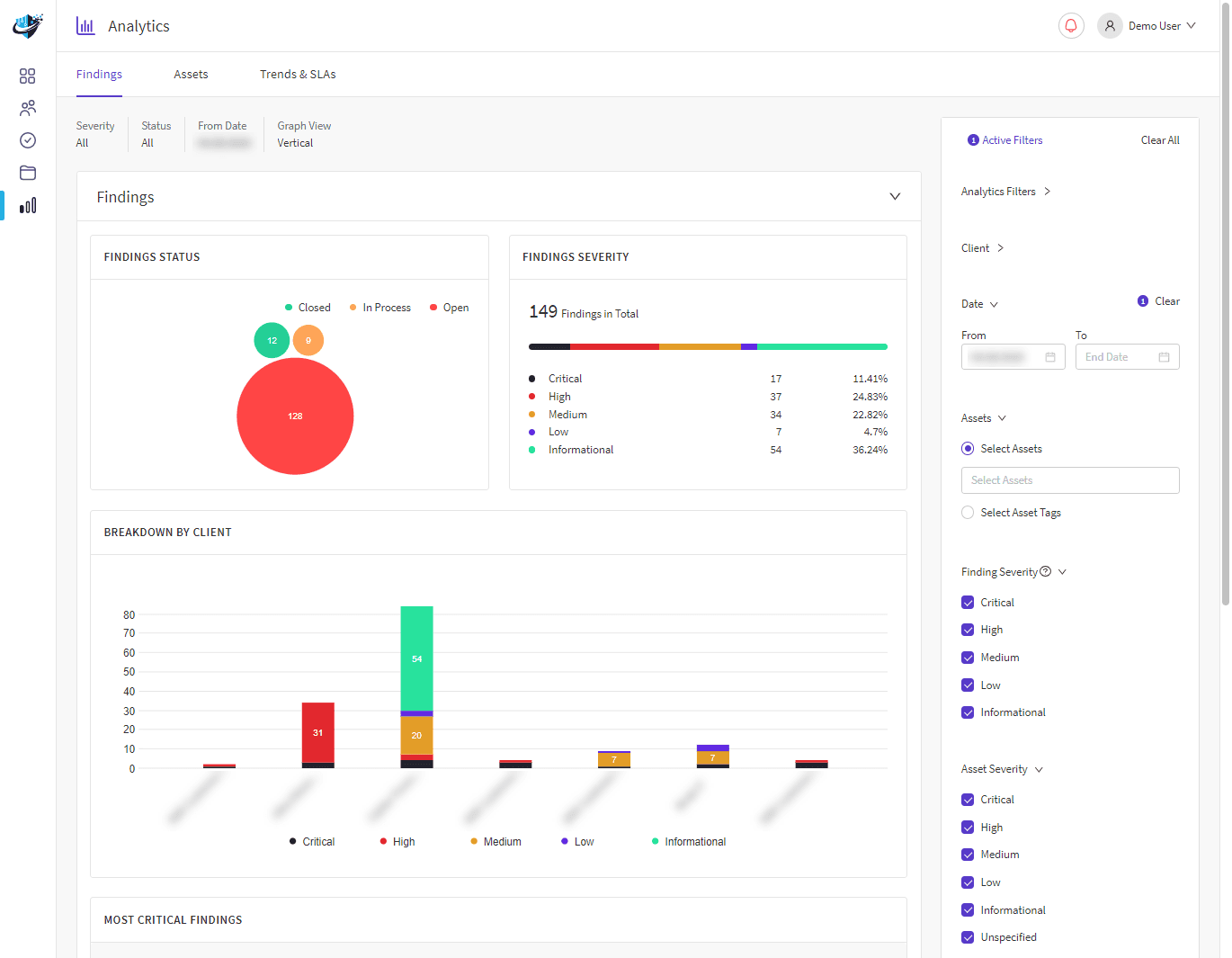
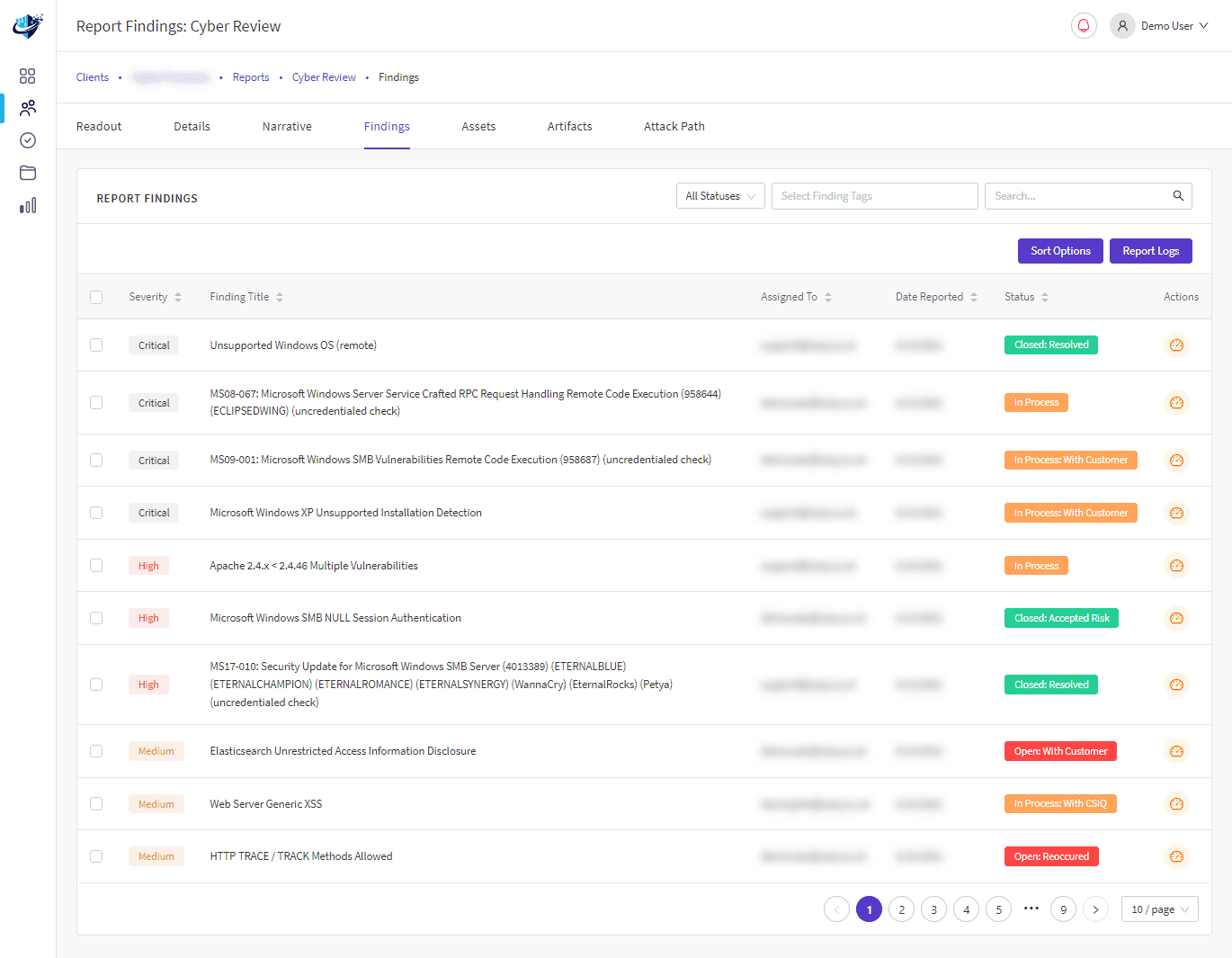
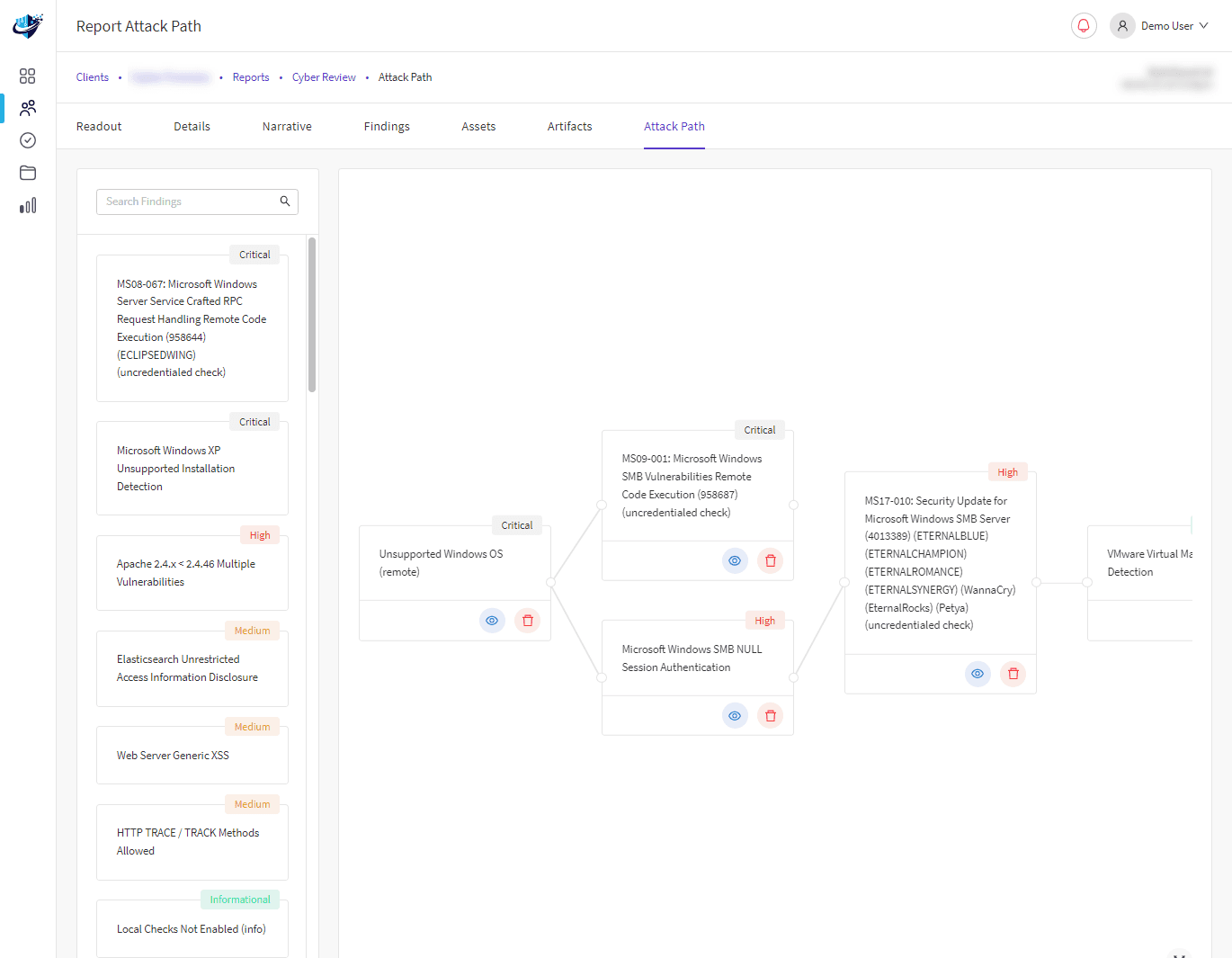
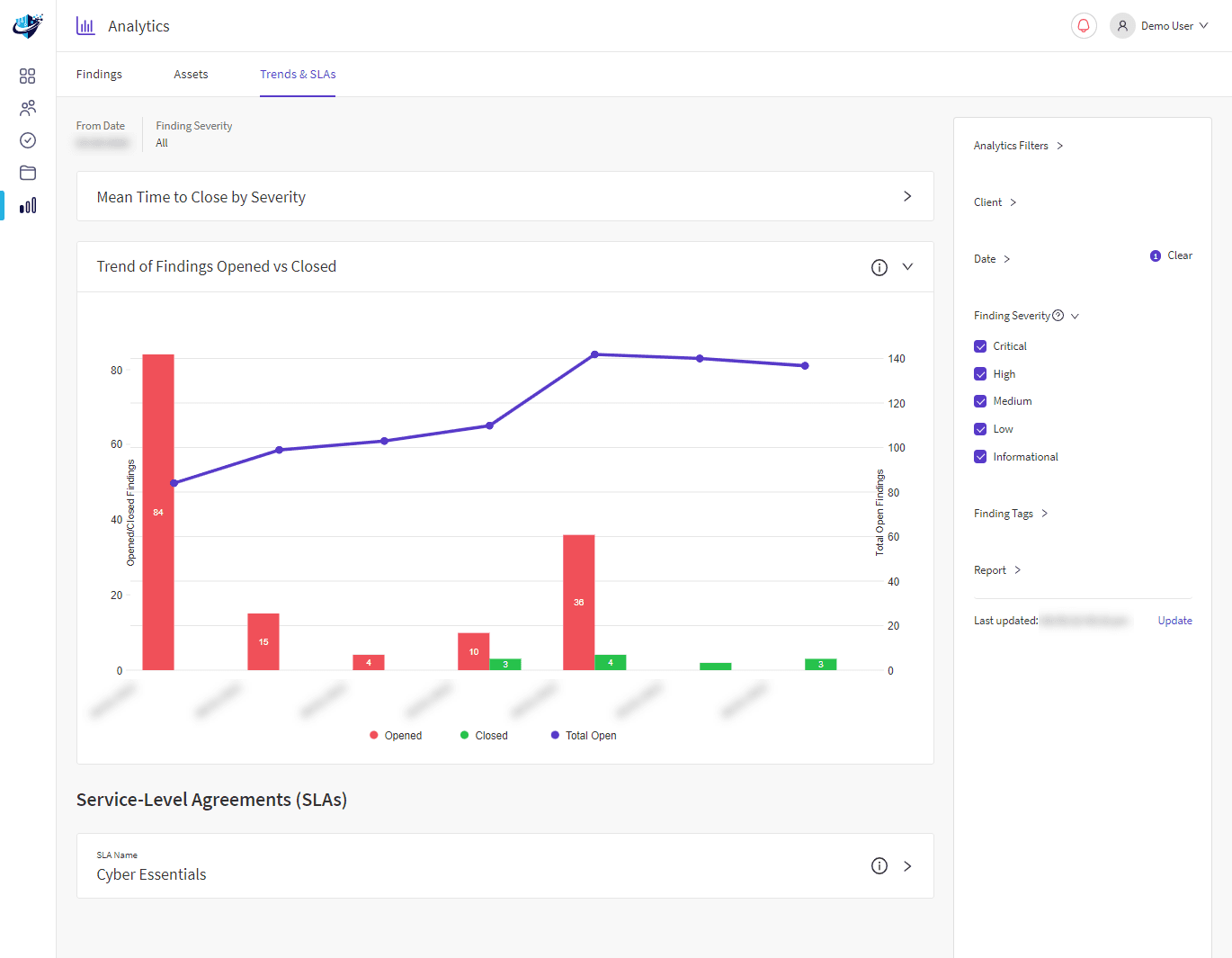
Penetration testing is a vital component of any cybersecurity strategy. It is used to identify, test and highlight vulnerabilities of an organisation’s Cyber security strength before cybercriminals and insider threats can exploit it.
It is essential to test your security posture regularly. However, it is time-consuming and expensive to maintain an in-house team of cybersecurity experts. That is where we come in. We offer comprehensive penetration testing services in the United Kingdom, with our experienced team offering invaluable advice on how you can improve your organisation’s security posture.