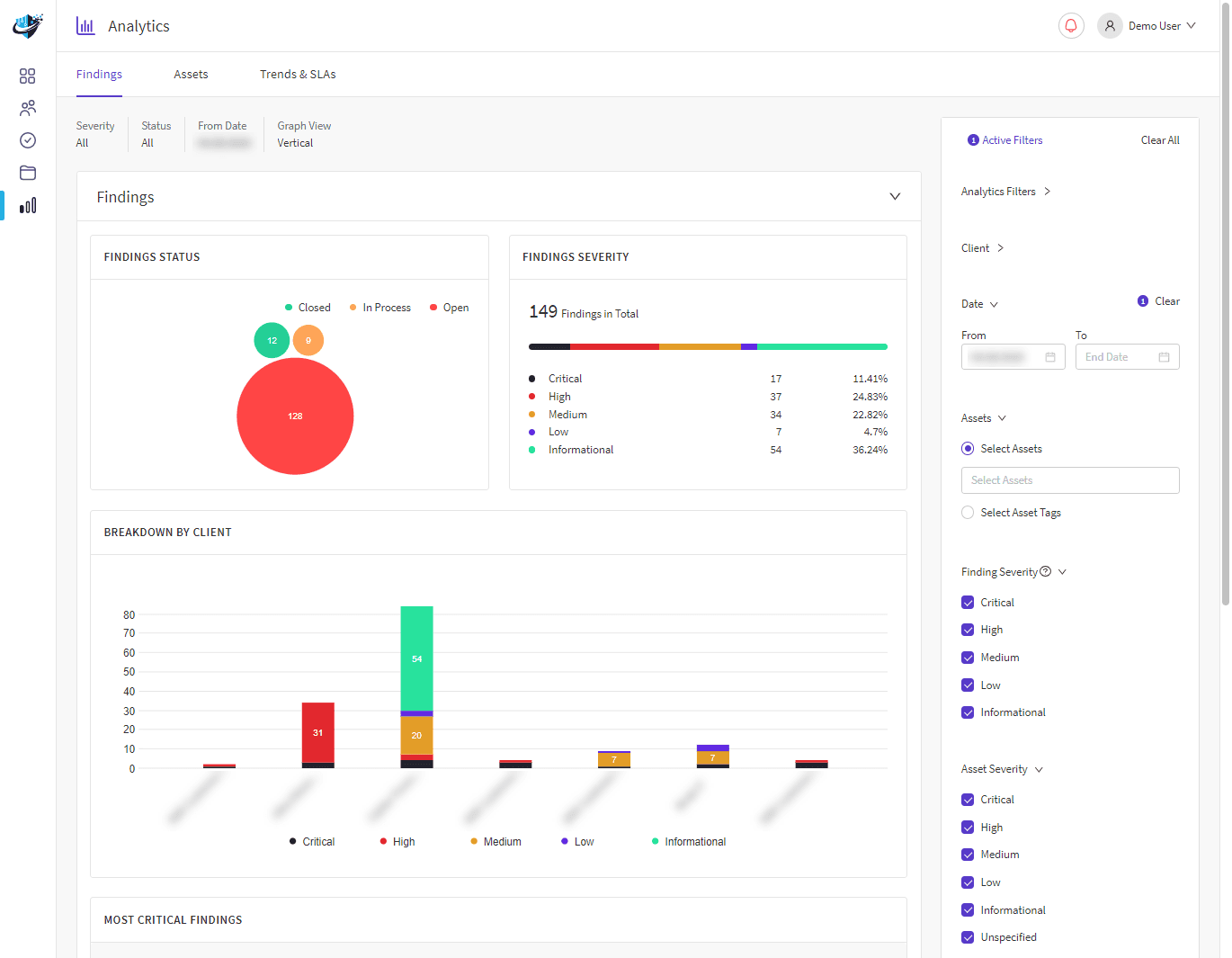
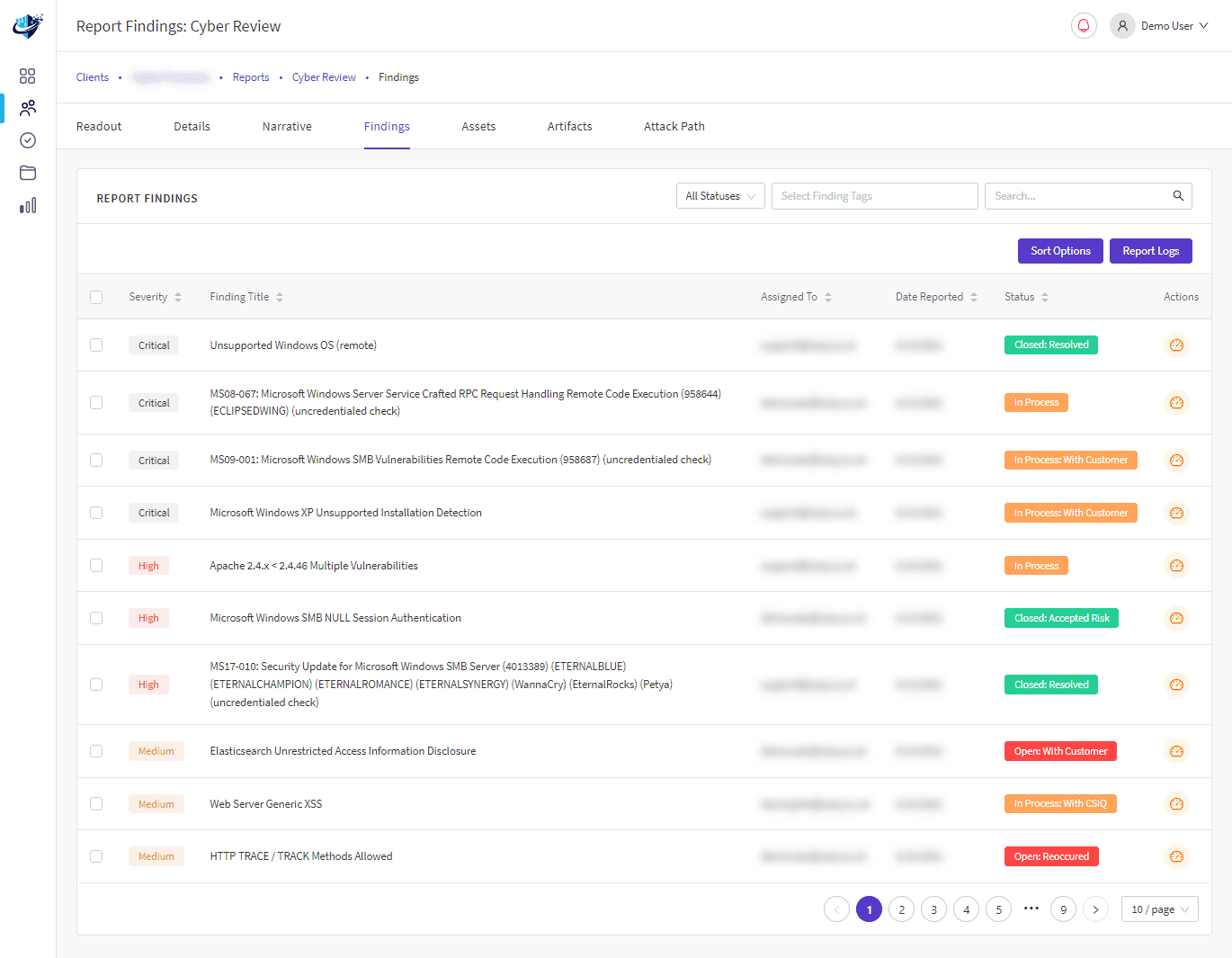
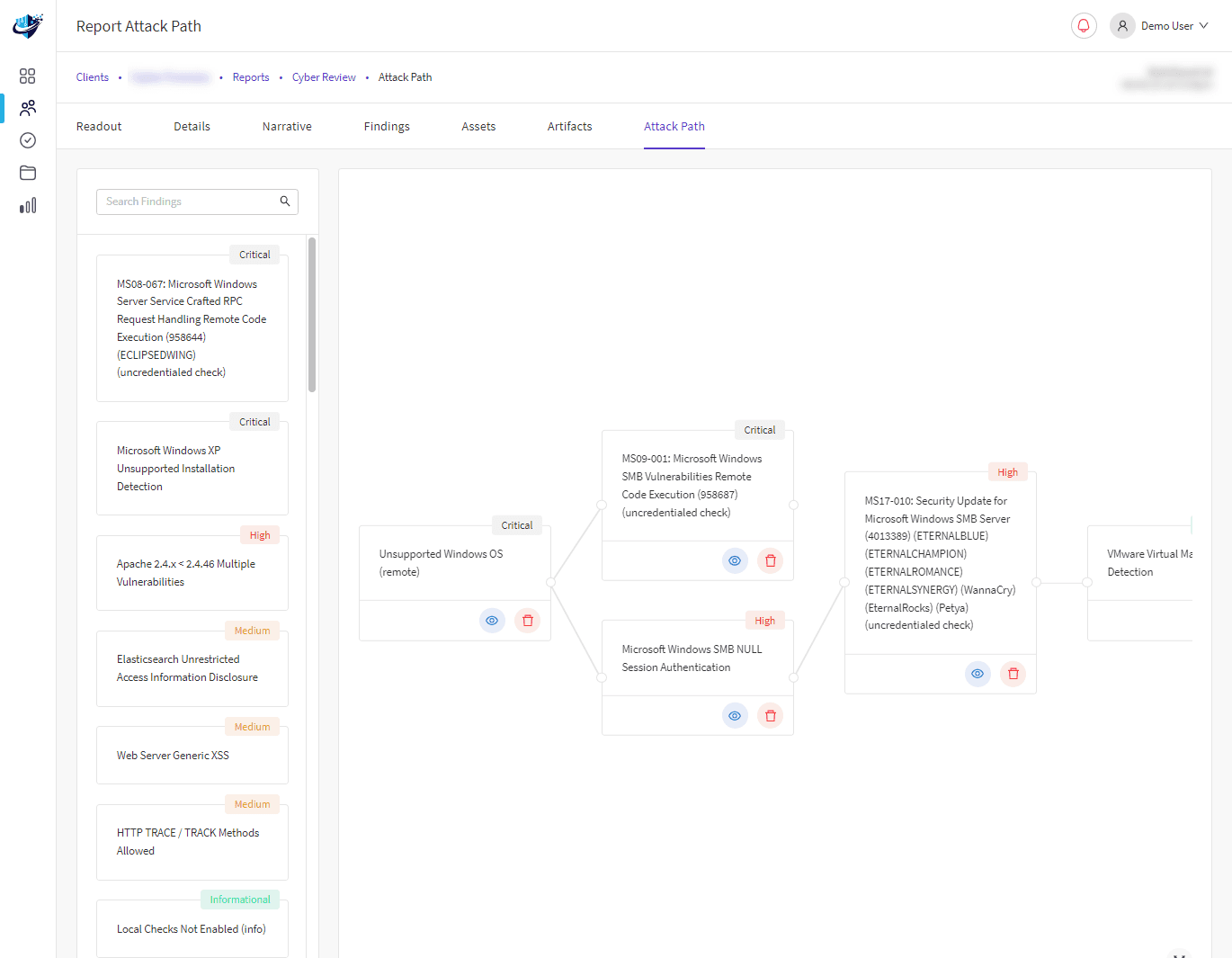
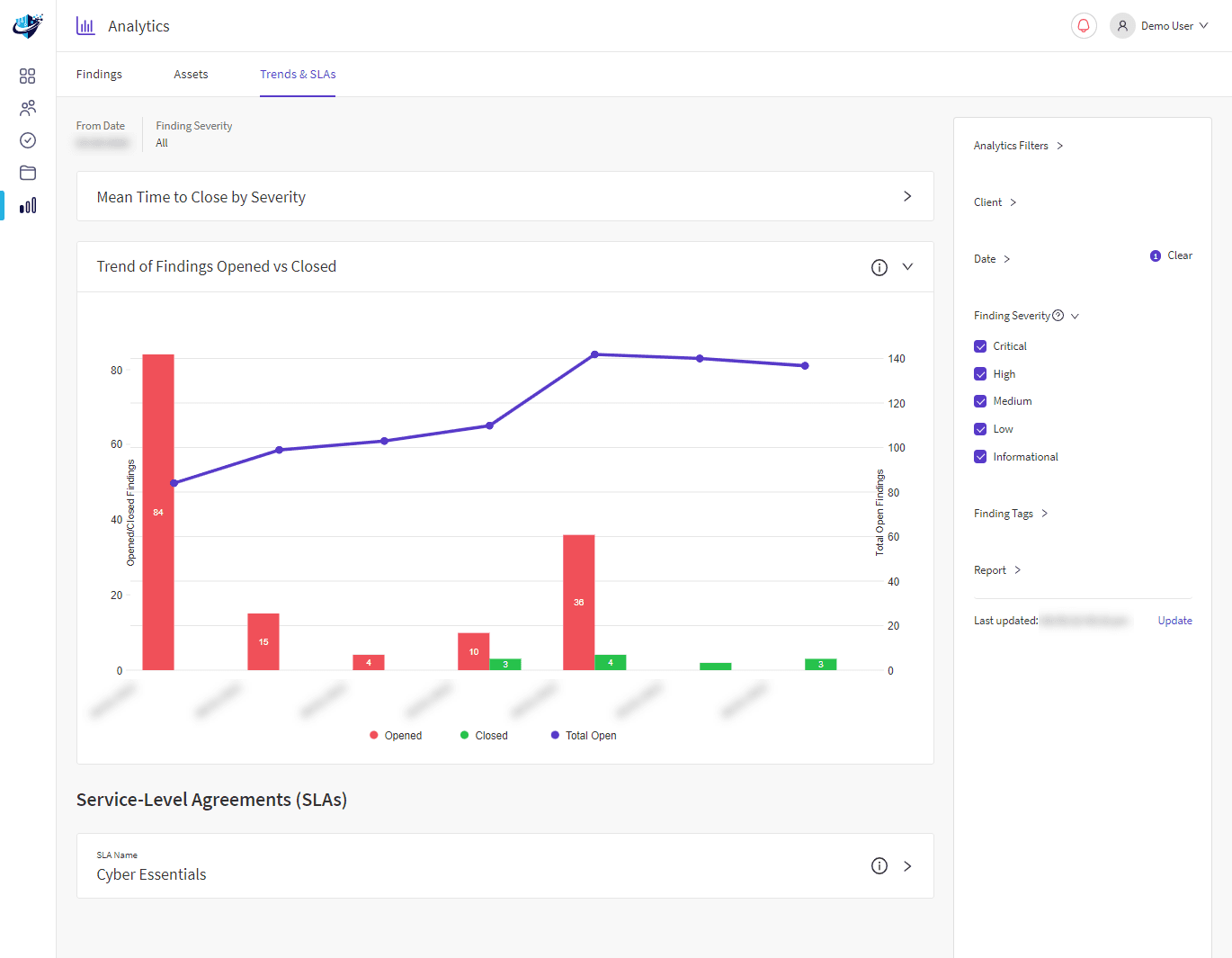
Security challenges are unavoidable as remote working solutions gain significance in today’s modern landscape. A remote desktop review highlights how Remote Desktop and Citrix Solutions are excellent business enablers, providing secure access to company data from any location.
We have many years of experience deploying and maintaining Remote Desktop Services (RDS) and Citrix security technologies. We test the best practices for remote desktop security to ensure your environment remains secure and operational, wherever you are.