Web Application penetration testing is an authorised security test on a web application to identify vulnerabilities within your network that can be exploited. Web applications are a common target for hackers and can be challenging to keep secure.


Why have Web Application
Penetration Testing?
The purpose of a web application penetration test is to give assurance of the application’s security. It tests manually for weaknesses in access controls, user permissions and separation, input injection, file upload/download functionality, authorisation, and authentication.
It can identify weaknesses that may allow an unauthorised or role-based user to use the application unintentionally and access the information they are not authorised to access.
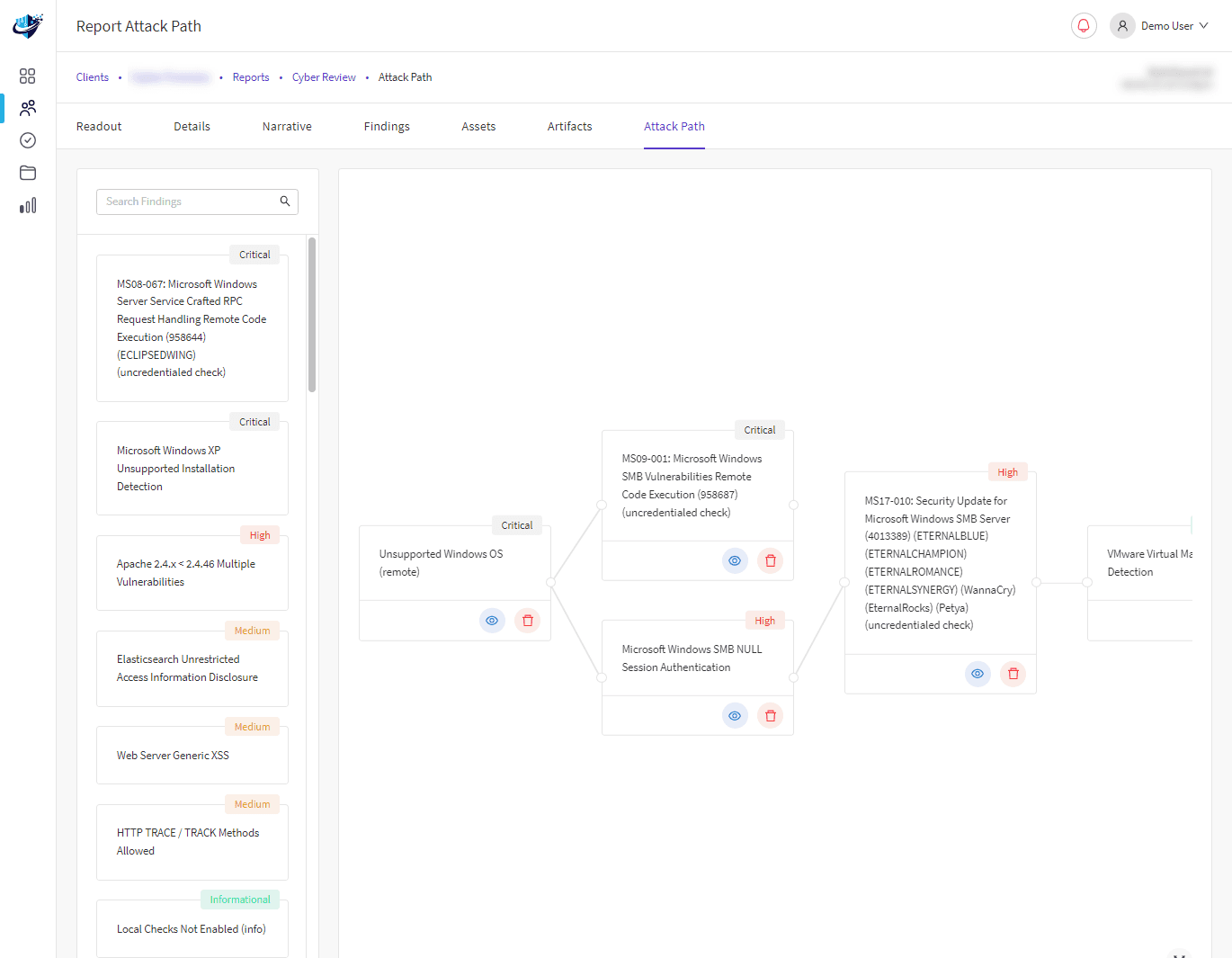
Our methodology will link any identified vulnerabilities at the protective layers to perform attack chaining, demonstrating real-world risks to your data.
What does it do?
It identifies vulnerabilities
It can identify any software development lifecycle issues
It helps to avoid reputation damage from a security breach
It provides evidence of due diligence for compliance and regulatory certification standards
It can give assurance to customers and suppliers that their data is protected
It goes beyond the capabilities of automated web application scanning and commercial tools
Who is it for?
Web application penetration testing services are intended for businesses that store, process, or transmit sensitive data through web applications.
Many hackers will compromise companies through web applications that are accessible over the public internet. Therefore, your business needs to be proactive with the security of these applications and remediate vulnerabilities promptly.
We provide advice and support for the life of any vulnerabilities identified, ensuring that you are supported throughout the remediation process and protecting your data.
What are the benefits of web application penetration testing?
- Gain real-world insight into your web applications protection mechanisms
- Ensure that untrusted data is separated from commands and the database
- Develop strong authentication and session management controls
- Confirm that sensitive and unintended information is not leaked

The OWASP Top 10 Web Application Issues
We combine the OWASP top 10 with our in-house methodology to ensure that our testing reflects the latest threats and trends in web application testing
Cyber Security Simplified
Our services are built to be cost-effective while maximising risk reduction. All consultancy and managed solutions provide actionable results that protect your business from opportunistic to advanced persistent threats.
12
34
35
Penetration Testing as a Service (PTaaS)
Our Pre-Pay contract, combined with a managed attack surface package and our professional penetration testing services, brings a full Cyber security service to protect your business from attacks and threats.
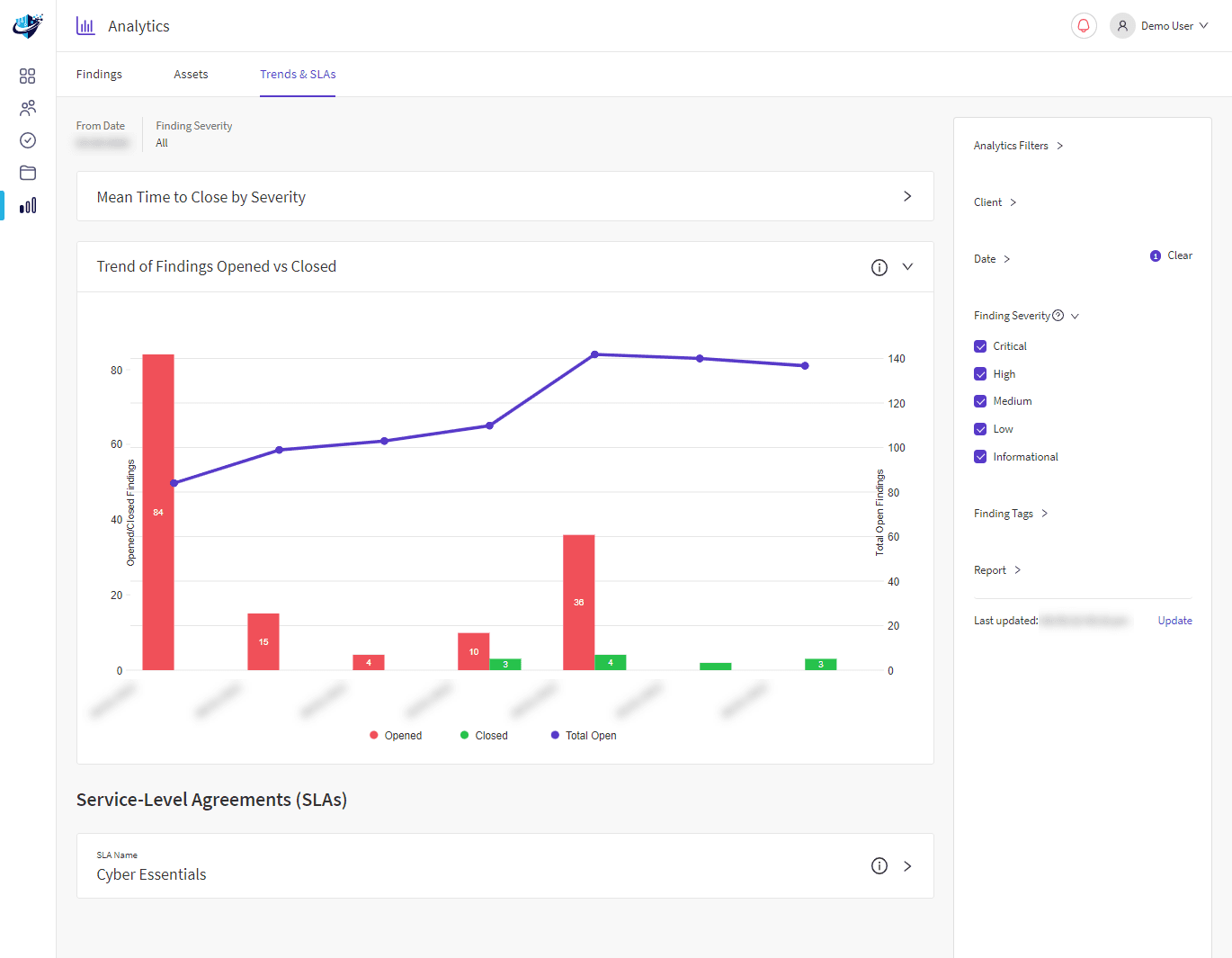
Businesses are often stuck in the loop of annual penetration testing and then waiting a year before retesting. With our PTaaS, our ongoing services significantly reduce the time it takes to identify an attack to days instead of months.
What are the Benefits of PTaaS?
- Continuous security monitoring to protect against emerging vulnerabilities
- Any new services introduced by the business are automatically assessed
- Managed by our SOC and Consultancy team
- CSIQ Insight – giving a full view of all identified security issues
- Reduces the time between identified vulnerability to remediation with dedicated support

Our Web Application Testing Methodology
Our Crest approved approach to penetration testing ensures that we identify critical weaknesses in your security posture.
Our process includes:
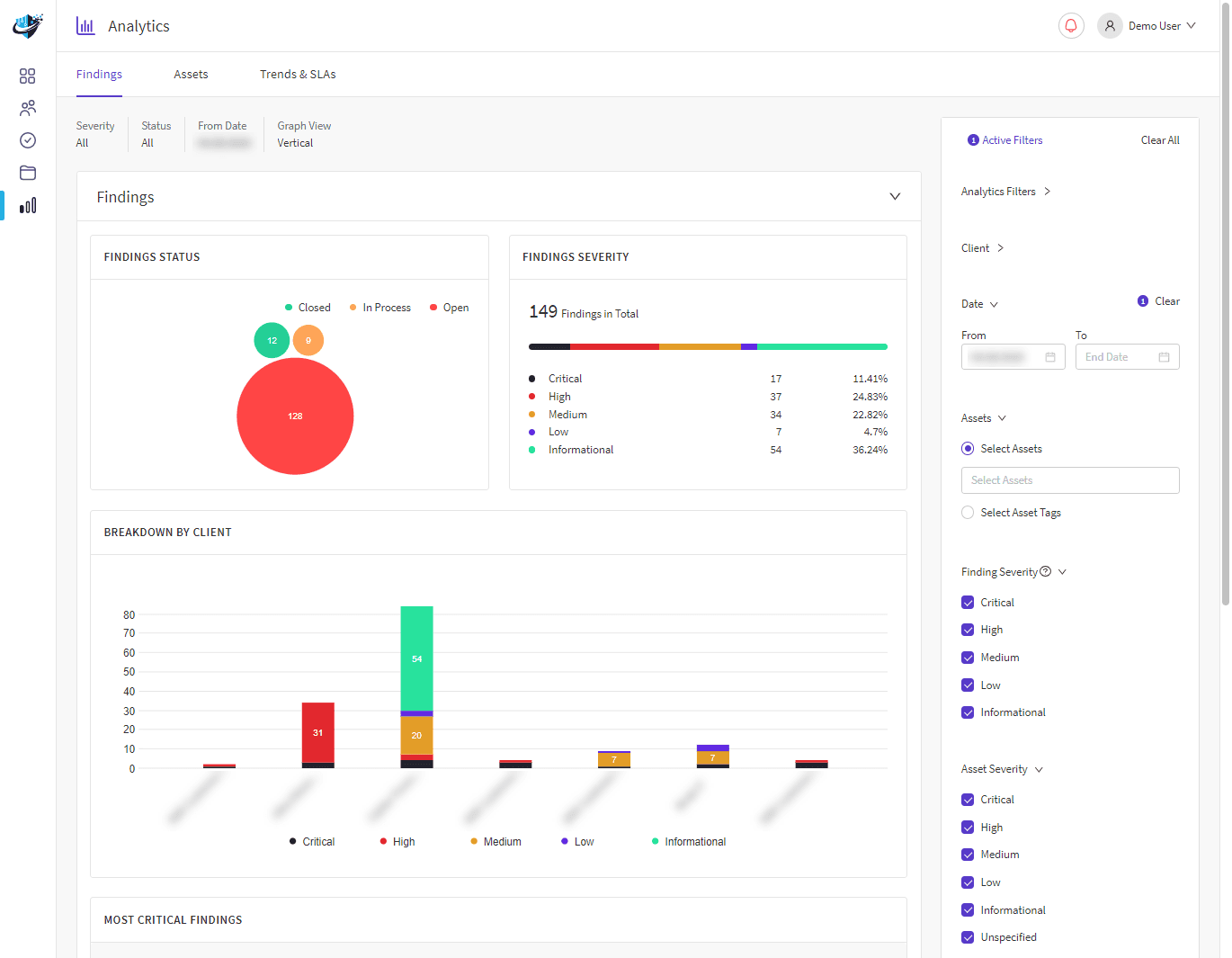
CSIQ Insight: Risk Management Portal
All consultancy and managed services include access to our Risk Management Portal.
Flexible Pre-Pay Contract
Benefit from 25% off and rapid response with our Pre-Pay Contract
Journey to Web Application Maturity
Journey to Web Application Maturity

Penetration Testing
Services
Need penetration testing? Visit our penetration testing page to see how we can help.
Or get in touch to find out more about all our available services.
Our Accreditations & Memberships
We are proud of our industry recognised certifications in Cyber Security and Service Delivery
FAQ
How frequently should I perform a penetration test?
Because cyber threats are always evolving, it is advised that web application penetration testing is performed at least annually.
CSIQ also recommends integrating vulnerability management into the secure development life cycle.
Can I track progress during the engagement?
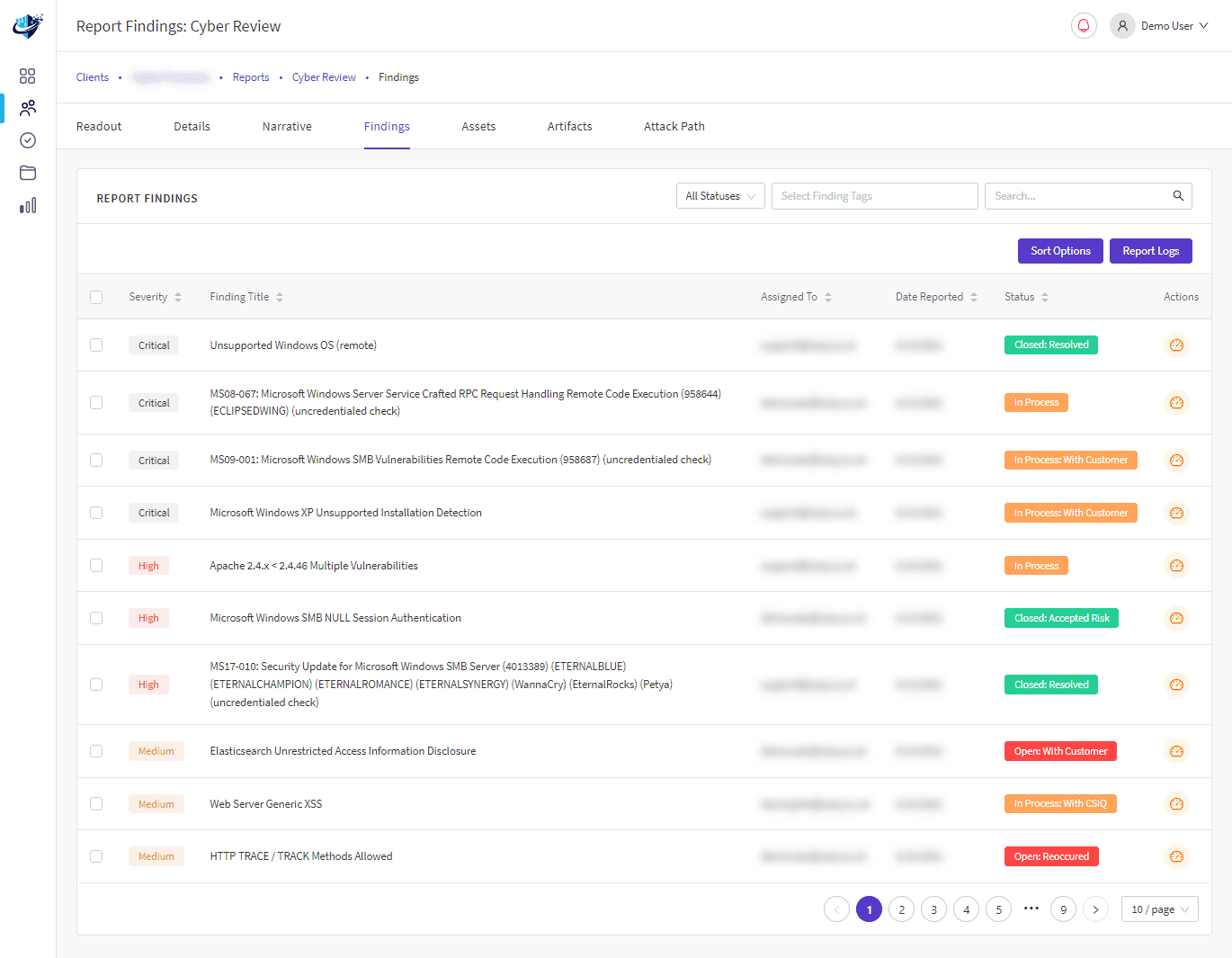
Yes. All penetration testing engagements include access to CSIQ Insight and our client portal, allowing you to track projects and vulnerabilities as they are discovered and until they are remedied.
What happens after the penetration test is complete?
After each engagement, the cybersecurity consultant assigned to the test will produce a custom-written report detailing the risks of any identified weaknesses, outlining recommended remedial actions prioritised by overall risk reduction.
In addition, CSIQ includes validation testing for all vulnerabilities identified.
Have a question for us about our services?
Send us an enquiry to get a rapid response from a cybersecurity expert.
Email Us
Call Us
"*" indicates required fields