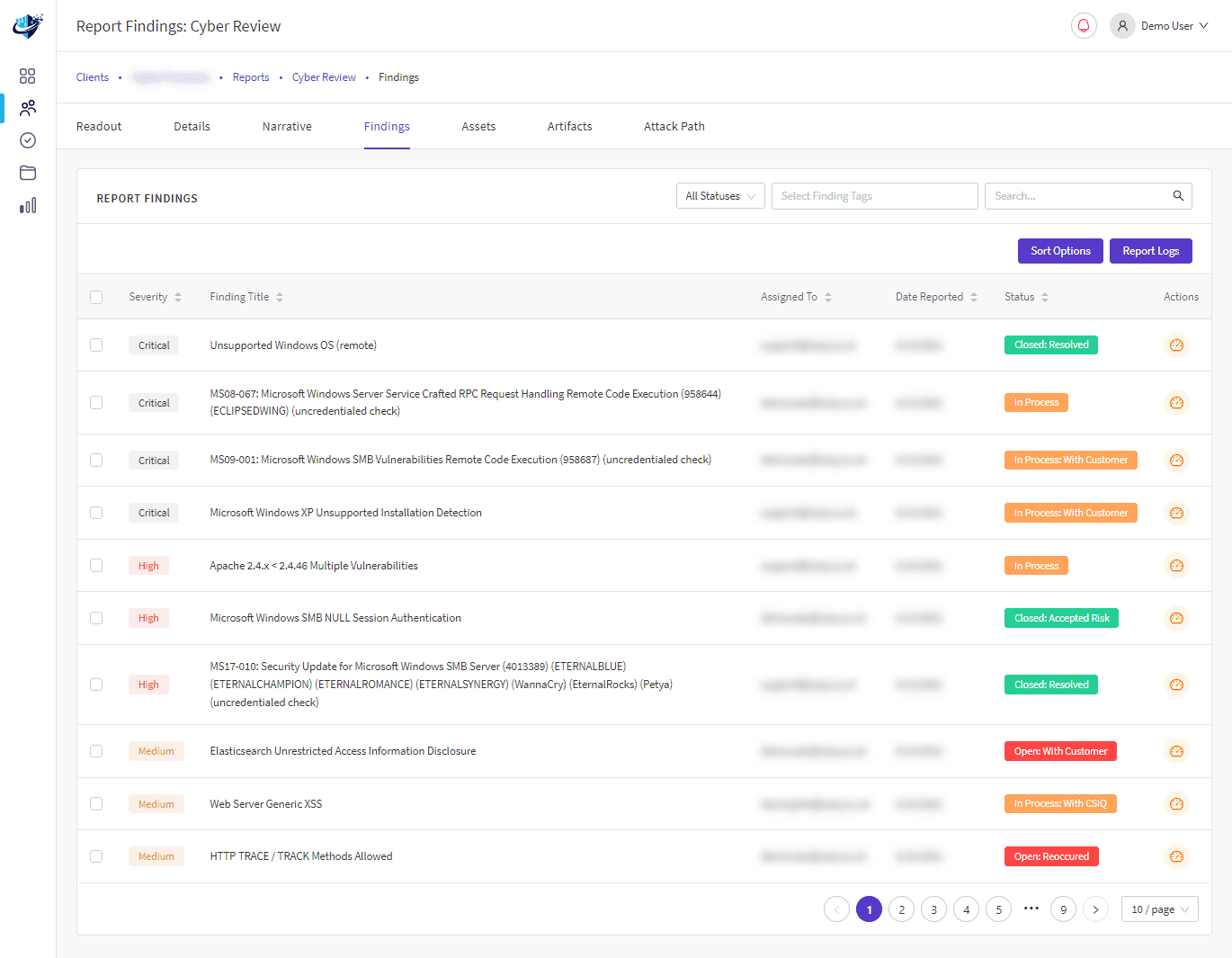
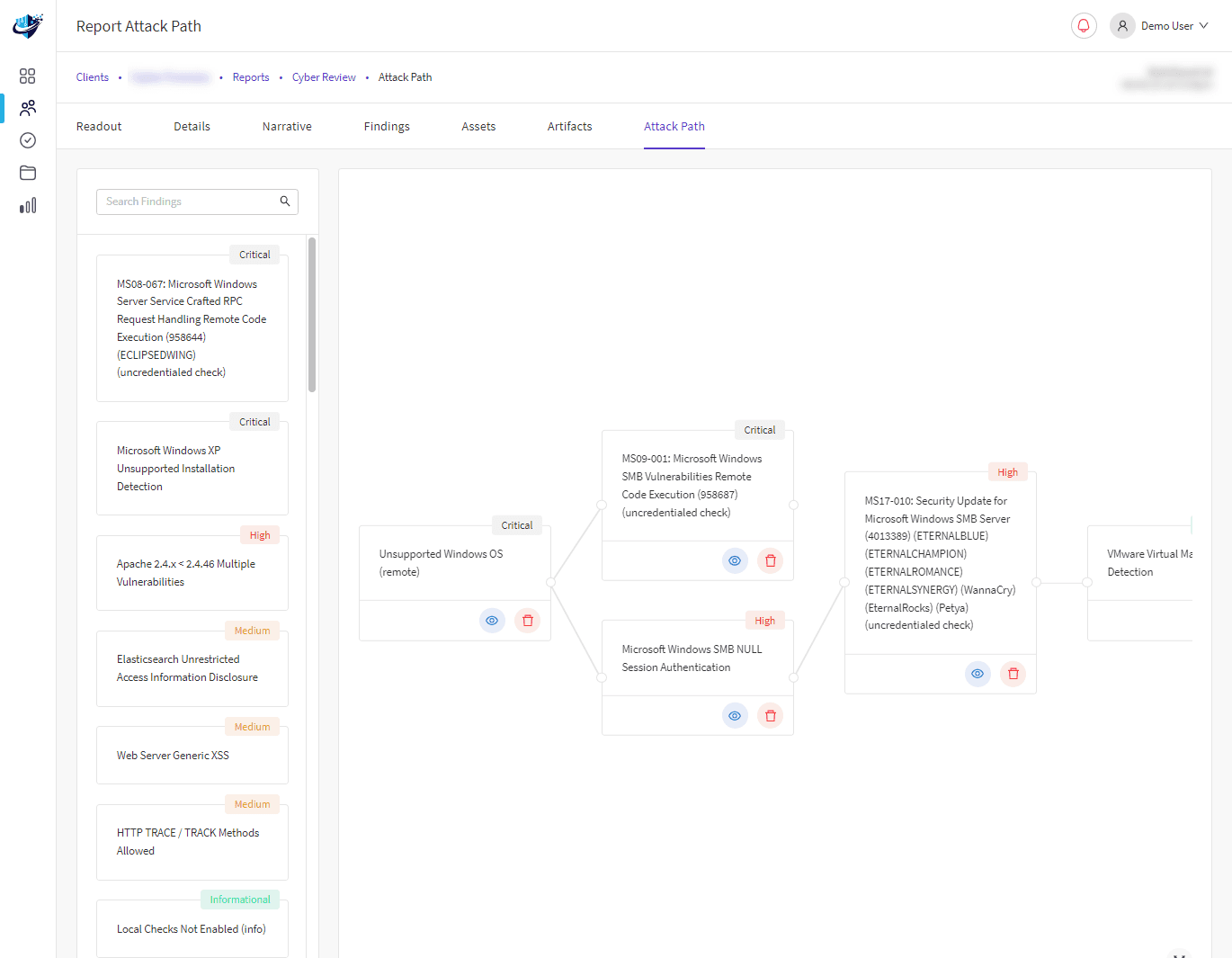
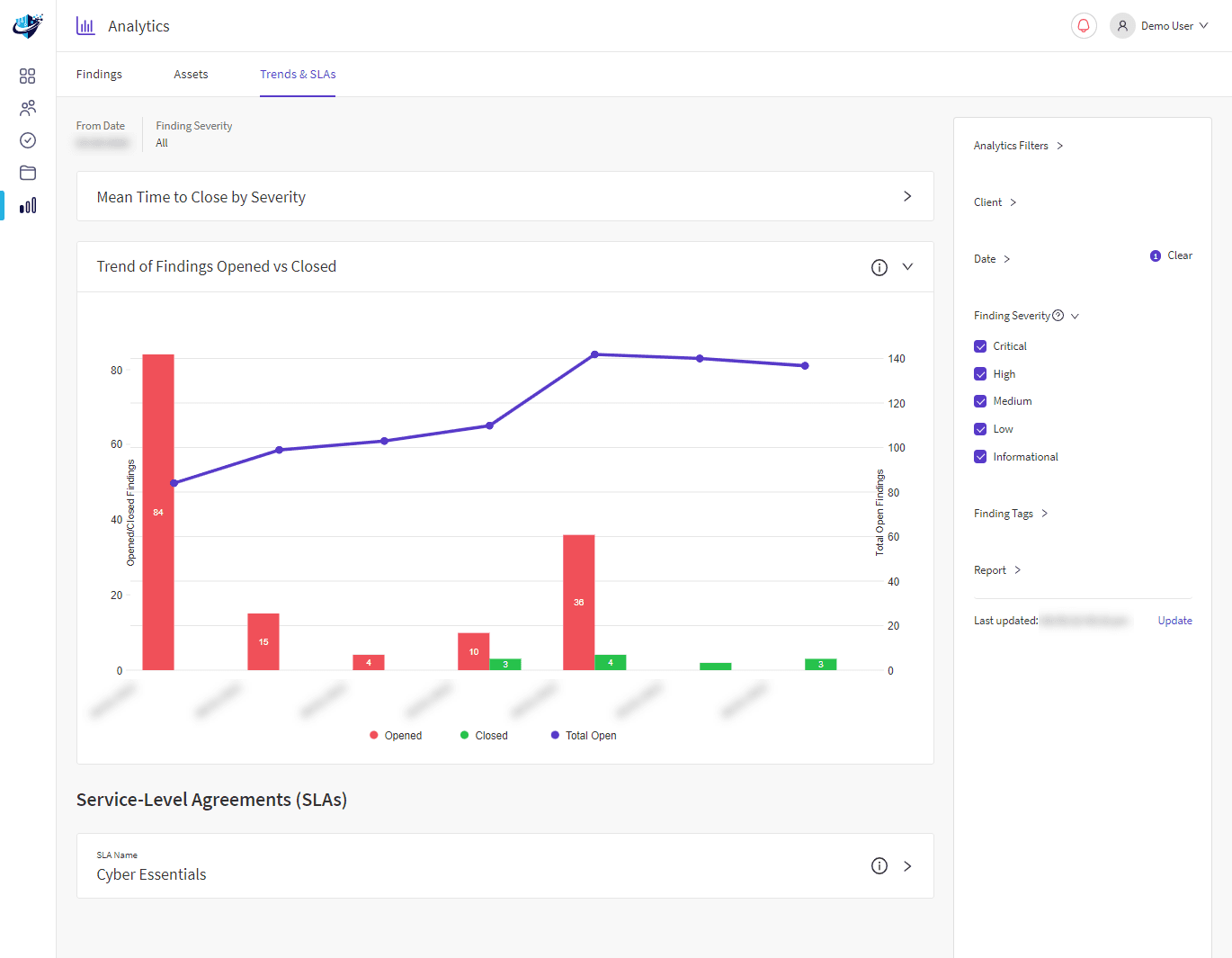
The rapid rise of cybercrime results from a lower technical barrier of entry for cybercriminals. Therefore, ensuring that your organisation is protected against disruption and reputational damage has never been more critical.
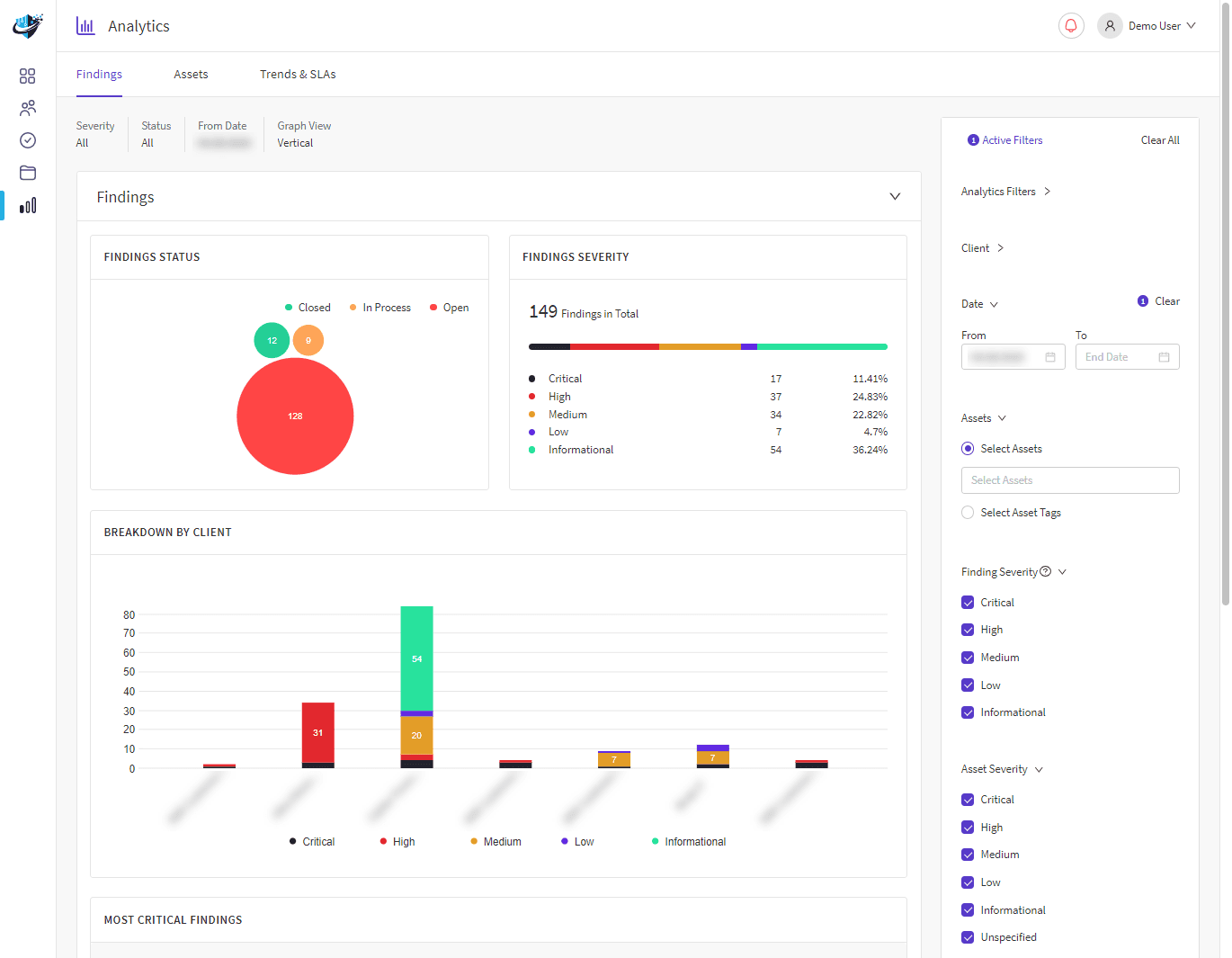
A Strategic Cyber Security Review will thoroughly assess the use of technology across the organisation. Our methodology will help you rapidly improve your company’s IT security stance with Cyber risk management strategies that will help your business face today’s cyber security threats.